Hospitals: 3 Digital Corners You May Be Cutting
By Jackie Flynn Sheckels, Kyle Clark, and Andrew George

The move from volume (fee-for-service) to value (value-based payment) and the growth in importance of outcomes and measurement are significantly impacting how providers share information with each other. Providers must be able to access health information across the continuum of care, as well as track and report health events amongst a network of providers. The FDA recently launched its Digital Health Innovation Action Plan, which reimagines the agency’s approach to digital health products and innovation, to promote greater access and improved public health.
Legally mandated shifts to digital record-keeping at hospitals and universities have come at each step of the patient-interaction lifecycle, from patient intake forms to office visit notes to laboratory test results, and especially to medical imaging. These records, once retrievable only by walking to a physical storage room and pulling a dusty physical folder, can now be called up with mere keystrokes and shared across the care continuum.
This is immensely beneficial to hospitals, doctors, and patients. A treating physician using digital tools can review test results or images on sophisticated computer systems that allow the operator to zoom in, change the color display to better distinguish regular anatomy from anomalies, or even create precise, computer-aided measurements of the size of foreign objects. These tools often provide quick and easy access to additional information that is essential to selecting the best treatment plan for the patient—when it’s done right.
When not done right, it also brings a host of new risks, like inadvertent changes to electronic diagnostic information and entry points for hackers to compromise medical devices. Dangerous corners are being cut in the digitization of medicine, with the potential for serious negative consequences for hospitals, doctors, and patients. Yet most are easy to fix—so long as hospitals know what to look for and take the time to check. Start with an audit of these three digital vulnerabilities:
Corner 1: Lost or Compromised Diagnostic Information
When paper records and images on physical film were kept in collapsible file folders, one could be reasonably certain that, even years later, the folder would still contain exactly what was put into it. While folders could and did occasionally go missing, physical tracking systems and limited access to the file room reduced this risk. Physicians were generally able to review historical patient encounters anew and hospitals could rely on these patient interaction records to conduct peer review and quality review inquiries, or to defend themselves in litigation. In the digital world, records can be inadvertently, even permanently, modified or deleted as part of the long-term archiving process due to incorrect settings or user error.
Downscaling
Two decades ago, one gigabyte of digital storage could cost as much as $100. To save money, digital imaging systems were set up to downscale the resolution of digital images before they were saved. These systems were also set up to save only the downscaled copies of digital images, with the originals permanently discarded. While the difference between the originals and the saved versions may not have been significant two decades ago, as the quality of digital images improved, that gap has grown significantly.
Take these test x-ray images from a hospital at the center of a criminal healthcare fraud case. Downscaling can be a significant problem—particularly if the doctor’s findings are going to be questioned by federal investigators years later.
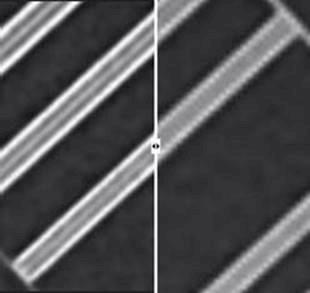
This issue has gone unnoticed by all but a few imaging specialists.[1] Were more hospitals aware of it, they would undoubtedly change their archiving settings. Today, one gig of storage usually costs less than a penny. The costs of defending against allegations of fraud or malpractice are considerably more.
User Error
It’s not enough for a hospital to have the right settings on its equipment. The operators of that equipment need to know how to use it correctly so that it fully captures and preserves what a physician saw when making treatment decisions.
We ran into this problem during a federal criminal investigation at a prominent hospital. Investigators examined patients’ coronary angiograms looking for ones that looked less blocked then had been recorded in patients’ medical records. Such cases, in the investigators’ view, were likely instances of fraud. In some of these questioned cases, however, the doctor had also performed a second test. Called an “intravascular ultrasound,” it gave a head-on view down the artery, allowing the doctor to make computer-assisted measurements of any blockage present.
Such computer measurements would all but end any accusation of dishonesty if they supported what the doctor had written—had they been saved.
In this case, the hospital had lost about 80 percent of its test results because staff did not follow the right steps to save them. For the 20 percent that were saved, the computer measurements vital to the doctor’s decision were gone. Some believed—inaccurately—that it was not possible to save these ultrasound measurements after a test was complete while others believed the measurements had been saved but never had a reason to check.
This failure to save vital evidence was not due to incompetence, but rather the predictable focus at a busy hospital on treating the next patient. In today’s enforcement environment, a close eye to information and data procedures and adequate personnel training are key.
Corner Two: Insider Threats
There is a misconception in the data security world that most insider threats pertain to a malicious intent and exfiltration of key information, like blackmail from an external party or an employee aiming for financial gain. More threats, however, stem from negligence. Top insider threats include general unrestricted access abuse to gain information for alternative and unsanctioned uses, data mishandling for a convenience factor, use of unapproved hardware and software.[2] In fact, insider breaches most often take the longest to discover. The below are examples of vulnerabilities based on individuals who have access to information within the organization’s firewall.
|
VULNERABILITY |
BREACH DESCRIPTION |
|
Medical Device |
The loss of patient information due to lack of equipment wiping controls. Devices (like an x-ray machine) have local storage, just like a laptop. |
|
External/Removable Media |
An incident executed from removable media or a peripheral device being introduced into the IT environment. |
|
Impersonation/Spoofing |
An email attack involving replacement of legitimate content/services with a malicious substitute. |
|
Improper Usage |
Any incident resulting from violation of an organization's acceptable usage policies by an authorized user, excluding the above categories. |
|
Loss or Theft of Equipment |
The loss or theft of a computing device or media used by the organization. |
The human element, when it comes to insider threats as well as external threats like ransomware attacks, presents the greatest cyber risk of all. The most important step to mitigating this risk is to implement proper access controls including file, directory, and network share permissions with the least allowable access rights in mind.
Corner Three: The Value-based Care Ecosystem
The healthcare sector is the only industry that combines highly valuable and sought-after bulk data sets of personal health information, personally identifiable information, payment information, medical research, and intellectual property. The shift to value-based systems of reimbursement, which requires coordination across transitionally siloed provider types within an episode of care, adds significant complexity to networks.
How could this trend lead to vulnerability for your hospital? Clinical integration across providers—who now have access to your systems—is leading to new and more complex data sharing and integration requirements. As noted in Cisco’s 2017 Midyear Cybersecurity Report, “as healthcare organizations bring more connectivity to their facilities and devices, security leaders are also raising concerns about the safety of converged networks. In the past, complex medical devices—such as the Picture Archiving Collection System (PACS), infusion pumps, and patient monitoring devices—typically arrived with data networks managed by vendors, so the devices were physically isolated from other networks. Today, with ample bandwidth available, healthcare organizations believe it’s practical to simply flow data through one network, and use logical segmentation to separate various network traffic types such as clinical devices and administrative and guest wireless networks. However, if this segmentation is not done properly, the risk of attackers gaining access to critical data or devices increases.”[3]
Aligning all providers in an integrated network requires a renewed focus on information and digital governance and monitoring with a clear understanding of where clinical partners sit and the respective various risk factors each could generate. Your security is only as strong as those other providers that exist within your ecosystem as they may not have adequate protection or processes from cyber threats.
Get Back on Track: Risk Assessment
Healthcare companies should consider conducting an enterprise risk assessment which incorporates cybersecurity issues to develop a baseline to assess the maturity of their current information governance program and determine areas of greatest exposure. Risk assessments can be executed in variety of methods and budgets, but on average, will take two to eight weeks to complete based on the size and complexity of the organization as well as the availability of the staff required to participate in the project.
A typical risk assessment will address five key areas:
- Data Governance Risks - Assesses risks related to: change management, business continuity, disaster recovery, and emergency management
- Records Control Risks - Assesses risks related to: records classification, document retention, document disposition, and storage management
- Legal/Regulatory Risks - Assesses risks related to: litigation readiness, regulatory compliance, monitoring of regulatory requirements, and legal holds
- Technology Risks - Assesses risks related to: information security, email management, software management, information management executive sponsorship, IT migrations, and decommissioning of systems
- Third-Party Risks - Assesses risks related to: external providers and devices accessing the IT network
At the conclusion of the assessment, the company will be provided recommendations for immediate and long-term remediation of risks, as well as a score of how their data management programs rank against industry peers. Recommendations may include prioritization of tasks based on key areas of risk, policy reviews, training guidelines, and identified data sources in need of better controls.
The end goal of conducting a risk assessment is to gain an understanding of vulnerabilities within the organization as it pertains to protecting patient information; however, the entity may also gain a better understanding of how they can protect their institution and staff using their information in the event of a regulatory action or litigation. Risk to your hospital cannot be 100 percent eliminated; only mitigated.
“The most significant impact the recent hacker attacks will have on the healthcare sector is that information security will need to be considered as an integral part of the security and operations processes of healthcare organizations. They will need to become more proactive and consider risk as equally as utility,” said Mitch Parker, CISO of Temple University Health System.
How else can healthcare organizations protect themselves?
A well-rounded and documented cybersecurity plan is crucial and should address the following:
- Data/network mapping and access control/management. Entities should know where all HIPAA information is stored, how it traverses the network, and the security around that data—who has access, who has control, and who has what privileges?
- Device monitoring. This is crucial when it comes to theft breaches; mobile device management (MDM) can alleviate some of these human error risks. Entities should know about every mobile device in their organization that contains personal health information (PHI).
- Third-party due diligence. Vendor systems can be an access point or weak link in an organization’s protection. Third-party risk due diligence must be done through the prospect, initiation, and ongoing relationship stages to isolate changes in risk and vulnerability postures.
- Top-down security mindset that supports staffing and training. Board members should be informed and proactive in taking ownership of cybersecurity. Organizations should ensure they have a dedicated information security function that reinforces cyber awareness throughout the organization.
- Well-documented policies, standards, and procedures. Providers should document their cybersecurity mindset and be able to produce specific guidance, like their cyber incident response plan, the types and frequency of network security tests performed, and training protocols.
Where do Risk Management and Lawyers Come in?
For hospitals, information risk management starts with the ability to locate and protect critical information assets, such as medical records, test results, legally protected personal information, and financial information, and requires departmental alignment with the Information Technology, Information Security, Staff Management and Legal. Areas where this team may collaborate may include policy assessment and enforcement, data flow analysis, data classification, data storage, third-party access to systems, data remediation, data migrations (and downstream effects), review of staff training processes and procedures for storing records, and data archival processes.
Historically, it has not been the responsibility of the in-house legal team to be involved in discussions of information governance and data management of internal systems. In the Losing Diagnostic Information scenario outlined above, in-house counsel may have made different decisions on legal strategy had he/she known of the complicating factors of how images were archived versus the original images viewed by the physician. Such nuances can even influence if an organization is willing to take a case to trial versus settlement. Access to the most accurate and up-to-date information is critical for crafting a strong defense position. In today’s digital record environment and as the standard of patient care has evolved, the role of in-house counsel has changed and now may include some oversight into how records flow and are stored throughout the organization.
Digital health creates tremendous opportunities for improved care, lower costs and better patient access. What is your hospital’s digital strategy? What are the specific risks, what are your organization’s capabilities, gaps, and resources? Are there digital corners being cut or under-resourced at your hospital? Are you even aware of the risks your hospital has exposure to within its boundaries, understanding the reach and digital footprint?
About the Authors
Kyle Clark and Andrew George are lawyers in the Litigation Department of Baker Botts’ Washington, DC office. They devote significant time to defending and advising hospitals and physicians on criminal and civil investigations led by Justice Department prosecutors. Their emails are kyle.clark@bakerbotts.com and andrew.george@bakerbotts.com , respectively.
Jackie Flynn Sheckels is a Senior Director in BDO USA’s Technology and Business Transformation Practice. Jackie routinely consults with large domestic and international clients in the health care, telecommunications, technology, government contracting, energy and education industries with regard to formulating defensible discovery strategies, data analytics, collection plans, data extraction, forensic analysis, and document review. She can be contacted at jflynn@bdo.com .
[1] See Eliseo Vano et al., Influence of Image Metrics When Assessing Image Quality from a Test Object in Cardiac X-ray Systems, 24 J. Dig. Imag. 331, 336–37 (2011); Roberto Sanchez et al., Influence of Image Metrics When Assessing Image Quality from a Test Object in Cardiac X-ray Systems: Part II, 25 J. Dig. Imag. 537, 541 (2012).
[2] Verizon 2016 Data Breach Investigations Report, Page 41.
[3] Cisco 2017 Midyear Cybersecurity Report, P.76.
