Eliminating The Vulnerabilities Of Connected Medical Devices
By Vinay Gokhale, Vice President of Business Development with Thirdwayv

In May 2019 an FDA safety warning about unauthorized automated insulin dosing systems highlighted a major vulnerability that is present in all connected medical devices. A flaw in an FDA-authorized insulin pump had enabled it to be re-programmed for use with an unauthorized device to create a customized treatment for Type 1 diabetes. Cybercriminals can exploit this same type of flaw to hijack these and other connected medical devices, access their data and alter health monitoring and other operations. The same vulnerability can be exploited to introduce counterfeit devices and associated consumables into the market.
Combatting these threats requires the same security-by-design model that has been proven in other mission-critical industries. This model ensures that all communications are secure, each system element can be trusted, and patients have the “always-on” connectivity that is vital for their health monitoring and treatment.
Cyber Threats Escalate
Threats will increase with patients’ growing desire to control connected-health systems using their own commercial smartphones. Many devices such as heart defibrillators, insulin pumps, and glucose meters can be wirelessly hijacked and reprogrammed. Once cybercriminals gain short-range access to an insulin pump, for instance, they can command it deliver the wrong insulin dose. They also can acquire sensitive information about a patient’s condition by intercepting data in these devices’ telemetry systems during transmission.
In a move to preempt these dangers, the FDA in October 2018 published a draft set of medical device cybersecurity guidelines for designing trustworthy devices. The guidelines also include recommendations for reducing the risk these devices pose to patients due to a loss of authenticity, availability, integrity, and confidentiality. The most effective way to implement these recommendations is with a security-by-design approach. In applications where medical devices will be controlled with and accessed by commercial smartphones, it also will be important that this approach also incorporate end-to-end, multi-layered protection against cybersecurity threats.
Peeling Back The Layers
The first of three basic security layers for trusted connected-health systems is application security. A secure communications channel is established between the smartphone app, the medical device, and the cloud, augmenting the built-in security mechanisms of popular operating systems such as Android and iOS. This ensures that authorized devices are resistant to a variety of malware and wireless channel cybersecurity attacks and can safely use the same Bluetooth connection found in any commercial smartphone to automatically connect to intermediate hardware gateways or smartphone apps that are within communication range.
The second layer ensures that only authorized and trusted sources can send information and issue commands. As part of this authentication layer, a unique digital cryptographic identity is given to all system elements for attestation, or the ability for each to validate the authority and privileges of the others. The trusted cloud infrastructure issues digital certificates over the air to authorized smartphone apps and medical devices and manages all identities throughout their life cycle on the system’s network.
The best way to implement the authentication layer is by provisioning a hardware security module (HSM) to each medical device at the factory. The HSM stores and manages the cryptographic keys and digital certificates that are used to identify devices. All device programming and final test are controlled throughout the manufacturing process. When devices are on-boarded into the connected healthcare system, they are pre-programmed to only interact in the field with approved gateways.
The third layer ensures the “always-on” connectivity that is critical for health monitoring and dosing systems. Connected-health solutions that depend exclusively on a handheld device or smartphone to deliver cloud connectivity cannot always achieve continuous data availability and device control. There is a dangerous risk that safety-critical data won’t reach the cloud, and commands won’t be received for controlling the medical device. The solution is a combination of gateways, including traditional fixed gateways and the use of the smartphone itself as a soft gateway.
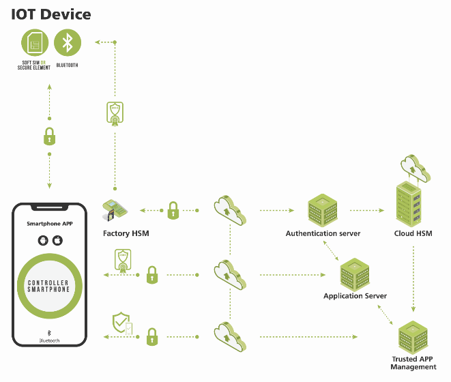
Figure 1:In this example using Thirdwayv’s end-to-end solution for a continuous glucose monitor (CGM) application, trust is added to every element of the system using the combination of a secure communications channel, authentication, and mutual attestation.
While it was previously a complex and cost-prohibitive undertaking for a medical device manufacturer to add this type of multi-layered security to its product offering, these capabilities can now be implemented using modular security software suites and HSM factory-provisioning services from a third-party cybersecurity technology provider. The availability of software development kits (SDKs) with all necessary application programming interfaces (APIs) facilitates rapid incorporation into a medical device developer’s solution.
About The Author
Vinay Gokhale is Vice President of Business Development with Thirdwayv.
