Connect And Protect: Zero-Trust Helps Secure Electronic Medical Records

By Christopher Logan, Senior Healthcare Strategist, VMware
The Zero Trust model of security, long a hot topic among CISOs, is being implemented today in healthcare. Virtualization, visibility, and automation in the software-defined data center make the approach practical, helping organizations minimize threats to patient data and safety, even as their digital care ecosystems expand.
When it comes to patient safety and care, quick and easy access to patient information — where and when it’s needed — is critical. At the same time, maintaining the security and integrity of that data is paramount.
With more than 80 percent of medical records now digitized, healthcare is working to be able to quickly serve up and share the right information, where and when it’s needed, to improve care, increase quality, reduce costs, and deliver a better patient experience.
Next-generation advances in sensors, mobility, integrated workflow, data analytics, decision support, and machine learning are rapidly expanding healthcare ecosystems and redefining what’s possible in digital care.
Growing Threat
But the very digital connectedness that enables more effective and efficient care also expands risk. Unavailable or blocked access to a patient’s medical data has forced providers to postpone time-sensitive procedures. The consequences of a data breach in healthcare go beyond identity theft—compromised data can put a patient at risk.
The number and sophistication of cyberattacks targeting healthcare, such as recent WannaCry and NotPetya ransomware and malware, keep growing. One study found that nearly 90 percent of healthcare organizations reported at least one data breach in the past two years — and almost half experienced five attacks or more.
Many factors make healthcare an attractive target. It stores large amounts of valuable personally identifiable heath and financial data. And it presents a broad attack landscape. EMR applications running on multiple servers in flat networks may have millions of ports open. Applications are increasingly integrated into end user workflows across multiple types of devices, including vulnerable legacy systems.
What’s more, healthcare, dealing with high rates of change, may not be as vigilant as other industries. Not only are IT budgets in general smaller in the healthcare industry — a smaller proportion of those budgets are spent on IT security. Research shows that healthcare spends 23 percent of IT budget on security, compared to 35 percent in other industries, such as utilities and telecom.
How can healthcare IT, with limited budget and staff, hope to be able to protect against growing threats across a rapidly changing and expanding digital ecosystem of devices, data, applications, and connections?
Zero Trust Model
One answer lies in a Zero Trust approach to IT security, first introduced by Forester in 2009.
In contrast to traditional IT security, in which a ‘trusted internal network’ is protected from the ‘untrusted external network’ by perimeter defenses, Zero Trust recognizes that in a connected world, the perimeter will—and must—be porous, making such an approach ineffective. Instead, Zero Trust advocates that no entity be trusted and that security be built into data center architecture, to protect from the inside out.
With the advent of software-defined data centers, the implementation of Zero Trust security has become practical. Virtual networks make it possible to build software-defined firewalling, routing, switching, and load balancing directly into the hypervisor—and thereby distribute policy-driven security into and across the entire environment.
Complementing the physical network segmentation traditionally used to comply with regulations such as HIPAA and PCI-DSS, virtual networks enable ‘micro-segmentation’ at the individual virtual machine level, to precisely control the lateral movement of threats across the data center (Figure 1). Even if an attacker makes it past perimeter security and into the network, they will be unable to move to other servers, dramatically shrinking attack vectors.
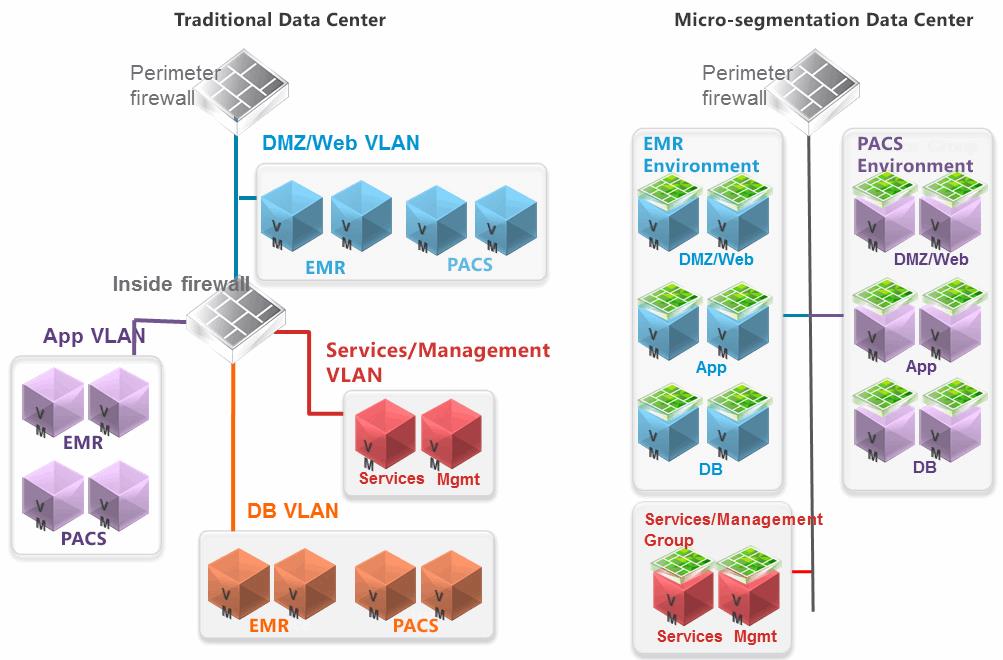
Figure 1. Traditional data centers protect at the edge, leading to too many open ports, exposing the entire network including EMR and PACS environments should a threat get past the hardware-based firewall. Micro-segmentation policies work in the virtual environment, enabling persistent security policies to limit traffic to only the nodes that need to communicate at any given time.
Used in conjunction with virtual desktop infrastructure (VDI) technologies and mobile device management solutions, micro-segmentation aids in furthering the Zero Trust model by securing clinician endpoints. End users and device applications are restricted to a ‘virtual tunnel’ into the data center, connecting only to the servers, applications or workloads that support them and prevented from accessing anything else on the network (and anything else on the network from accessing them).
Simplifying Security
Networking and Security teams gain greater granularity, flexibility, extensibility, and scalability, as well as end-to-end visibility, analytics, and automated control of the virtual environment, simplifying security in ever more complex, connected, and fast-changing healthcare environments.
Virtual, micro-segmented networks can be layered on any kind of physical network topology and have no impact on routing or switching protocols. The underlying physical network continues to operate while virtual network security micro-segmentation is applied or modified.
Policy-defined controls automatically follow and protect workloads wherever they go. For example, if a workload migrates to the cloud, its security policies follow. If IT spins up a new pool of desktops in the virtual layer, security policies automatically attach.
At Work Today
A growing number of healthcare providers — including Nebraska Medicine and Interfaith Medical Center — are using virtual network micro-segmentation to implement Zero Trust security models that reduce the threat landscape and to better secure EMR, mobile, and patient and provider services today.
As Christopher Frenz, Director of IT Infrastructure at Interfaith Medical Center says: “Given the expansion of EMR applications and the increasing number of connected devices, the more segmented our network is, the better off we are. That way, threats—especially those that compromise patient safety — can’t move laterally within the data center. We can make critical patient data more readily available while keeping it secure. It’s a huge advantage that allows us to deliver more innovative treatments, empower patients to take a more active role in their own care, improve and meet healthcare outcomes, and meet compliance requirements.”
